Information Technology Security
IT Security helps to protect University systems, services, and data against unauthorized use, disclosure, modification, damage, or loss by utilizing security policy, processes, technologies, and awareness to provide a secure IT environment that supports the University's mission of education and community outreach. Information and procedures included are modeled after many of the policies and procedures in place with LSU's IT Security and Policy team.
Email Security Best Practices
Email is an integral form of communication at LSUE, allowing our students, faculty and staff the ability to collaborate quickly and easily. Despite its convenience, email is susceptible to attacks that can compromise your account, personal information, and your entire computer. It is important to use e-mail with caution and to understand its inherent risks to protect yourself from common threats such as spam, phishing, and viruses. Here are some ways you can protect yourself:
Use Caution with Email Attachments
Never open or download an attachment from an unknown source. Attachments may contain viruses that can compromise your computer and personal information, and therefore must be approached with caution.
Keep your software up to date. Keeping software current on your machine can protect your computer from attached viruses that exploit vulnerabilities of older software.
If an attachment is related to Microsoft Office (e.g., Excel, Word, PowerPoint) and it requests you to enable Macros, please do not enable them until you are sure that the attachment is legitimate.
Be Aware of Phishing Scams
Phishing is an attempt by a malicious actor pretending to be a legitimate enterprise for the purpose of stealing private information, such as usernames, passwords, social security numbers, and other sensitive data.
Learn about the Phishing Emails.
Be Mindful of What Information You Send Via Email
Never send personal information such as passwords, social security numbers, or credit card numbers via email. Email should not be treated as a secure communications channel for sensitive data.
Never Reply to Spam Emails
Do not reply to any email from an unknown source. Doing so may expose you to more spam in the future.
Create a Strong Email Password
Learn about Password Best Practices
What is Identity Theft?
Identity theft occurs when someone uses another person's personal information such as name, Social Security number, driver's license number, credit card number, or other identifying information to take on that person's identity in order to commit fraud or other crimes.
How to Protect Yourself from Identity Theft
The following tips can help lower your risk of becoming a victim of identity theft.
- Protect your Social Security number. Don't carry your Social Security card or other cards that show your SSN. Read "Your Social Security Number: Controlling the Key to Identity Theft".
- Use caution when giving out your personal information. Scam artists "phish" for victims by pretending to be banks, stores or government agencies. They do this over the phone, in e-mails, and in postal mail. Most institutions wouldn't ask for your SSN or other personal information over the phone, and many emphasize that they do not ask for this information. Do not send your SSN or credit card information via email. If you wouldn't feel comfortable putting this information on a postcard, you probably wouldn't want to send it by email either.
- Treat your trash carefully. Shred or destroy papers containing your personal information including credit card offers and "convenience checks" that you don't use.
- Protect your postal mail. Retrieve mail promptly. Discontinue delivery while out of town.
- Check your bills and bank statements. Open your credit card bills and bank statements right away. Check carefully for any unauthorized charges or withdrawals and report them immediately. Call if bills don't arrive on time. It may mean that someone has changed contact information to hide fraudulent charges.
- Check your credit reports. Review your credit report at least once a year. Check for changed addresses and fraudulent charges.
- Freeze your credit. If you do not plan on conducting any activities that require third parties to run a credit report of you, you can freeze your credit reports. This will prevent attackers from obtaining credit histories and opening new lines of credit. You can learn more about credit freeze here - https://www.consumer.ftc.gov/articles/0497-credit-freeze-faqs.
- Stop pre-approved credit offers. Pre-approved credit card offers are a target for identity thieves who steal your mail. Have your name removed from credit bureau marketing lists. Call toll-free 888-5OPTOUT (888-567-8688).
- Ask questions. Ask questions whenever you are asked for personal information that seems inappropriate for the transaction. Ask how the information will be used and if it will be shared. Ask how it will be protected. If you're not satisfied with the answers, don't give your personal information.
- Protect your computer. Protect personal information on your computer by following good security practices.
- Use strong, non-easily guessed passwords.
- Use firewall, anti-virus, and anti-spyware software that you update regularly.
- Download software only from sites you know and trust and only after reading all the terms and conditions.
- Don't click on links in pop-up windows or in spam e-mail.
- Use caution on the Web. When shopping online, check out a Web site before entering your credit card number or other personal information. Read the privacy policy and take opportunities to opt out of information sharing. Only enter personal information on secure Web pages that encrypt your data in transit. You can often tell if a page is secure if "https" is in URL or if there is a padlock icon on the browser window.
Steps to Take if Your Data Becomes Compromised or Stolen
Credit Reporting Agencies: If you have reason to believe your personal information has been compromised or stolen, contact the Fraud Department of one of the three major credit bureaus listed below. Individuals whose personal information was involved in this incident may request a fraud alert to be placed on their credit files by calling any one of the three major national credit bureaus or completing an online form. Submit one online form request and all three agencies will add the fraud alert.
- Equifax
Direct Line for reporting suspected fraud: 800-525-6285
Fraud Division
P.O. Box 740250
Atlanta, GA 30374
800-685-1111 / 888-766-0008
http://www.equifax.com - Experian
Direct Line for reporting suspected fraud: 888-397-3742
Credit Fraud Center
P.O. Box 1017
Allen, TX 75013
888-EXPERIAN (888-397-3742)
http://www.experian.com - Trans Union
Direct Line for reporting suspected fraud: 800-680-7289
Fraud Victim Assistance Department
P.O. Box 6790
Fullerton, CA 92634
Phone: 800-916-8800 / 800-680-7289
http://www.transunion.com
When contacting the Credit Reporting Agency, areas of focus would include:
- Instruct them to flag your file with a fraud alert including a statement that creditors should get your permission before opening any new accounts in your name.
- Ask them for copies of your credit report(s). (Credit bureaus must give you a free copy of your report if it is inaccurate because of suspected fraud.) Review your reports carefully to make sure no additional fraudulent accounts have been opened in your name or unauthorized changes made to your existing accounts. NOTE: In order to ensure that you are issued free credit reports, we strongly encourage you to contact the agency's DIRECT LINE (listed above) for reporting fraud. We do not recommend that you order your credit report online.
- You may want to ask about the option to freeze your credit. Forty-seven states and the District of Columbia have enacted legislation allowing consumers to place "security freeze" on their credit reports. A consumer report security freezes limits a consumer reporting agency from releasing a credit report or any information from the report without authorization from the consumer.
- Be diligent in following up on your accounts. In the months following an incident, order new copies of your reports to verify your corrections and changes, and to make sure no new fraudulent activity has occurred.
- If you find that any accounts have been tampered with or opened fraudulently, close them immediately. To ensure that you do not become responsible for any debts or charges, use the ID Theft Affidavit Form developed by the Federal Trade Commission (FTC) to help make your case with creditors.
You may request an annual credit report from AnnualCreditReport.com as recommended by the Federal Trade Commission.
Social Security Administration
SSA Fraud Hotline: 800-269-0271
http://www.ssa.gov/
If you are the victim of a stolen Social Security number, the SSA can provide information on how to report the fraudulent use of your number and how to correct your earnings record. We encourage you to contact the SSA Fraud Hotline immediately once you suspect identity theft. The website also provides tips on using and securing your Social Security number. Visit the SSA website for advice on keeping your number safe. Additionally, you should create an account on SSA website regardless of your retirement age.
ID Theft Clearinghouse
1-877-ID-THEFT (1-877-438-4338)
Call the ID Theft Clearinghouse toll free at to report identity theft. Counselors will take your complaint and advise you how to deal with the credit-related problems that could result from identity theft.
Local Law Enforcement
It is important that you report identity theft to your local police department as soon as you become aware that you are a victim. Get a copy of the police report which will assist you when notifying creditors, credit reporting agencies, and if necessary, the Social Security Administration (SSA).
Resources
The following links provide detailed information related to identity theft and protecting yourself.
- Department of Justice
- Federal Trade Commission
- Privacy Rights Clearinghouse Identity Theft Resources
- National Consumer League's Fraud Center
- Identity Theft Resource Center (888-400-5530)
This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License (CC BY-NC-SA 4.0). It is attributed to Dean Woodbeck and Valerie Vogel, and the original version can be found on the Internet2 site available here - https://spaces.internet2.edu/pages/viewpage.action?pageId=50528489
Creating a strong password is key to protecting your personal information at LSUE. In general, the longer and more diverse a password is, the more difficult it will be for an attacker to crack it. LSUE Bengal Account passwords expire and must be changed every 180 days.
OIT recommends several best practices to help strengthen your credential for your LSUE accounts, in addition to other accounts a user may own:
- Use at least 8 characters and ideally a minimum of 14:
- In general, the longer the password, the harder it will be for an attacker to guess.
- Use a variety of characters:
- Use at least 3 types of characters including numbers, upper case letters, lower case letters, and/or special characters (e.g @, #, $, %)
- Never use part of your name:
- Passwords should not contain part of your name.
- Never re-use passwords:
- Do not use passwords repetitively swapping back-and-forth between previously used values.
- Create a passphrase:
- Passphrases are phrases that you can easily remember and can also be translated into characters. For example, the phrase “I saw Mike the Tiger at LSU in 2006” can be translated to “iSmtT@LsUi2006”.
- Never share with others:
- Anyone with access to your password has access to your personal information, and therefore can impersonate you online. This includes being able to alter your financial information, make purchases, send emails addressed as you, etc.
- Use different passwords for different accounts:
- If the same password is used across multiple applications and an attacker manages to get access to your password, they can then compromise all of your accounts with that one password. Using different passwords for different applications ensures that all of your accounts won’t be compromised if one of your passwords is cracked.
- Change your password periodically:
- Changing a password periodically allows for less time for attackers to obtain a particular password.
Use these criteria to determine which data classification is appropriate for a particular information or infrastructure system. A positive response to the highest category in any row is sufficient to place that system into that classification.
NOTE: If a new system is being implemented that will store or handle Confidential Data, you MUST inform the Office of Information Technology.
|
Confidential Data |
Private Data
|
Public Data |
|
| Legal Requirements | Protection of data is required by law (i.e. HIPAA, FERPA, GLBA, etc.) | LSUE has a contractual obligation to protect the data | Protection of data is at the discretion of the owner or custodian |
| Reputation Risk | High | Medium | Low |
| Other Institutional Risk | Information which provides access to resources, physical or virtual | Smaller subsets of protected data from a department | General University information |
| Access | Only those individuals designated with approved access, signed non-disclosure agreements, and a need-to-know | LSUE employees and non-employees who have a business need-to-know | LSUE affiliates and general public with a need-to-know |
| Examples |
Student education records Individuals’ health records and information Prospective students Personally identifiable financial information Campus Security systems and details Credit card numbers Certain management information Social Security Numbers Government restricted and/or classified Information LSUE ID numbers Financial transactions of students and employees Personnel Records (Although certain records contained within employee personnel files may be “public records” subject to disclosure, personnel files should be maintained as confidential data and disclosure of “public records” shall only be made after a case-by-case determination.) Information resources with access to confidential data
|
Information covered by non-disclosure agreements Materials for performance of official duties Proprietary information of LSUE or others contained within proposals, contracts, or license agreements
|
Campus maps Personal directory information (e.g., contact information) Departmental websites Academic course descriptions News Information posted on University website Budgets Purchase Orders
|
Although certain records contained within employee personnel files may be “public records” subject to disclosure, personnel files should be maintained as confidential data and disclosure of “public records” shall only be made after a case-by-case determination.
What is Sensitive Data?
Students, faculty, and staff interact with data on a daily basis. It is important to understand that all data cannot be treated equally in terms of how we store, share, and dispose of it. LSUE categorizes data in three ways:
- Confidential Data is the most sensitive classification and LSUE students, faculty and staff are required
by law to protect it. Examples of confidential data would include:
- Student Records
- Social Security Numbers
- Credit Card Numbers
- Health Records
- Financial Records
- Private Data is not considered confidential, but reasonable effort should be made so that it does
not become readily available to the public. Examples of private data would include
- Personal Contact Data
- Proprietary information
- LSUE ID
- Research Data
- Public Data is suitable for public consumption and protection of the data is at the discretion
of the owner. Examples of public data include:
- Public budget data
- Employee contact data
- Departmental Websites
How can I protect Sensitive Data?
Encryption is the most effective way to protect your data from unauthorized access. Encryption can be defined as transforming the data into an alternative format that can only be read by a person with access to a decryption key.
If you are transmitting sensitive data, you must use an encrypted communication channel. For example, with web based transmission, always ensure that the web site is protected by SSL. For FTP transmissions, make sure you are using a secured variety of the protocol (i.e. SFTP or FTPS).
Another available option is FilestoGeaux, which is a web-based temporary storage service that allows LSUE faculty and staff through myLSU to upload files they want to share to a secure LSU web server.
How should I dispose of Sensitive Data?
Eventually it may become necessary to dispose data or devices containing LSUE data. When doing so, remember the following:
- Disposing media (disks, tapes, hard drives) that contains confidential information must be done in a manner that protects the confidentiality of the information.
- Shred paper based media with confidential data when it is no longer needed. Do not discard confidential information in the trash.
- Do not take confidential information off campus unless it is encrypted.
Additional Guidelines
Here are some additional things to consider when dealing with LSUE data:
- Do not transmit confidential data via wireless technology, email, or the Internet unless the connection is secure, or the information is encrypted.
- Password protect all confidential data, and accounts with access to confidential data.
- Do not share passwords and do not write passwords down.
- Do not store unencrypted confidential information on PDA, laptop computer/desktop computer's hard drive, USB drive, CD, flash memory card, floppy drive, or other storage media.
- Eliminate the use of forms that ask for confidential information whenever possible.
- Do not store confidential information obtained from LSUE systems on media or other systems unless required by the University or by law.
- Always lock computers, offices, desks, and files that contain confidential information when unattended.
- Do not publicly display confidential data, or leave confidential data unattended.
- Do not share confidential documents or information with anyone unless required by government regulations, specific LSUE job responsibilities, or business requirements. Be prepared to say "no" when asked to provide that type of information.
- Do not communicate confidential information to others unless you know they are approved to handle confidential information.
- Notify the Office of Information Technology (OIT) and the data steward if you suspect confidential information may have been compromised.
If you have any doubts or questions about confidential information, please reach out to OIT at it@lsue.edu.
In an IT environment, data is stored on various forms of storage media (e.g., hard drives, USB flash drives, CD-ROM’s, tape drives). When you no longer need to use this storage media, the data must be securely removed to prevent unauthorized access. In compliance with FERPA, University policies and state legislation, this becomes imperative if the data is of a sensitive nature.
Why must the data be removed?
There are several reasons for removing the data from storage media before disposing of it. One of the reasons could be that the device hosting the data is being replaced with a newer model. Or perhaps the backup data on CD-ROMs and tapes are no longer needed and need to be expunged. Or maybe the hard-drive on the computer system is inoperable and needs to be replaced.
In each of these cases, the department responsible for the data on the device must ensure that all data is securely removed to minimize the risk of possible compromise of the data.
Why deleting the data is not enough?
There are several ways the data can be deleted from a computer system. The most common way is to grab and drop a file into the recycle bin (trash can) in modern operating systems and then empty the bin. However, the files being deleted are not the actual data, they are just pointers to the files and deleting these does not necessarily remove the data. The data remains on the hard-drive as unallocated space. There are sophisticated methods that can be utilized to retrieve the data previously stored on the hard-drive even if the unallocated space has been utilized by new files.
It is a common misconception that by formatting the hard-drive, all data has been securely deleted. Like delete and emptying the trash folder, this utility only modifies the file system but does not remove the data. Think of this as removing the table of contents from a book but leaving everything else. All the pointers are gone, but the pages still exist.
CD-ROMs provide a different challenge due to their read-only nature. The challenge is that there are no means to securely delete the contents of the CD. Inoperable hard-drives can also provide challenges as they cannot be connected to a system and approached through software.
Secure methods of deleting data
As previously mentioned, one cannot rely on deleting the data alone and it is important to remember that there are devices that present special challenges. So, now the question becomes what steps or utilities are available to us to securely delete and/or destroy the data.
Wiping Utilities
There are several utilities available to us that can perform the task of disk wiping. Disk wiping is a term that describes a utility's ability to write a series of 1’s and 0’s over the disk in an effort to securely remove the data. Some examples of commonly used utilities are DBAN, East-Tec’s Eraser, and Sourceforge Project Eraser. The task of disk wiping might be time consuming depending on the speed and/or performance characteristics of the computer. Please contact OIT for assistance.
SSD Data Security
SSD drives and other flash media store and handle data a little differently than hard drives. This makes the traditional advice of disk wiping and secure deletion less effective. It may still be possible to recover data from SSDs that have been wiped with a utility like DBAN.
One of the best ways to keep data secure on an SSD is to utilize full disk encryption. If the disk is protected by sufficiently strong encryption, the risk of data exposure is mitigated without using wiping tools.
Microsoft’s BitLocker and Apple’s FileVault can be utilized to encrypt the disk, and then the disk can be formatted. Without the original key, none of the data that was on the drive can be recovered.
If these steps are not possible, or the drive is inoperable, the SSD or flash media should be physically destroyed. Physical destruction of LSUE owned property is not permitted, therefore, if an LSUE department has identified that physical destruction is the only option available, the department must contact OIT who will then contact LSU's Office of Property Management.
Degaussing
Degaussing is a process by which the storage media is subjected to a powerful magnetic field to remove the data on the media. It is important to note that this method can make the media inoperable. Therefore, if you plan to reuse the media or sell the media, you should not use this method to securely remove data.
Additionally, degaussing is only effective for magnetic-based storage like older hard drives and tapes and is not guaranteed to work. Unless the drive is damaged or inoperable, it is preferable to use secure erasing or overwriting methods above to wipe the data. Destruction may be a better alternative for inoperable media.
Remember, flash based media, like SSDs and flash drives, cannot be degaussed. Hybrid hard drives that contain both traditional, magnetic storage platters and flash-based storage, are not good candidates for degaussing.
Destruction
For storage media that cannot be wiped (e.g. inoperable hard drive, DVDs) or that has contained highly sensitive data or for devices that cannot be degaussed (CD-ROMs, SSD drives, flash drives, etc.), destruction of media is the most effective means to ensure that the data cannot be recovered. There are several methods through which destruction of media can be achieved. Some examples are shredding disk platters, grinding the surfaces off of CD’s, and incinerating back-up tapes. Physical destruction of LSUE owned property is not permitted, therefore, if an LSUE department has identified that physical destruction is the only option available, the department must contact OIT who will then contact LSU's Office of Property Management.
The list of Data Owners, Data Stewards, and Contacts who provide management and oversight of the established data areas is indicated below.
| Area of Data | Data Owner | Data Steward | Contact |
| Advising and Registration | Donnie Thibodeaux | Marjana Herring | Donnie Thibodeaux |
| Authorized Course Master | Donnie Thibodeaux | Marjana Herring | Kimberly Smith |
| Admissions | Donnie Thibodeaux | Marjana Herring | Sonya Galloway |
| Athletics | Jeff Willis |
Jeff Willis Marjana Herring |
April Fontenot |
| Board of Regents | Stephen Heyward | Marjana Herring | Marjana Herring |
| Student Financials | Audwin Donatto | Marjana Herring | Audwin Donatto |
| Directory - Employee | Courtney Fruge |
Courtney Fruge Marjana Herring |
Jennifer Thibodeaux |
| Directory - Students | Donnie Thibodeaux | Marjana Herring | Donnie Thibodeaux |
| Facilities | Melonie Ceaser | Marjana Herring | Marjana Herring |
| Financial Aid | Jacqueline LaChapelle |
Selina Rene Marjana Herring |
Jacqueline LaChapelle |
| ID Cards | Stephen Heyward | Marjana Herring | Sandra King |
| Police/Security | Cory Lalonde |
Cory Lalonde Marjana Herring |
Cory Lalonde |
| Recruiting | Chad Jones | Chad Jones | Chad Jones |
| Residential Housing | Chad Jones | Victoria Throop | Victoria Throop |
| Security Access Management | Stephen Heyward | Marjana Herring | Marjana Herring |
| Student Case Management | Jacqueline LaChapelle | Jacqueline LaChapelle | Jacqueline LaChapelle |
| Student Records | Donnie Thibodeaux | Marjana Herring | Donnie Thibodeaux |
Multi-factor authentication (MFA) provides an extra layer of security to faculty and staff accounts by ensuring only you can approve valid log in attempts to your account. Multi-factor authentication pairs something you know (like your password) with something you have (like a cell phone, phone number, or other device that can verify you) to ensure that an attacker cannot login to your account without access to both methods.
After MFA is configured for your account, faculty and staff will be asked to verify your sign-in during certain off-campus log in attempts to make sure that you, and only you, can log in to your account and access your personal and private data.
Currently, applications utilizing utilizing LSUE's Microsoft Office 365 authentication services (faculty/staff email, OneDrive, Teams, Zoom, etc) are protected by MFA.
Whether it is your first time setting up MFA for your account, or you just need to update your phone number or make an adjustment, the MFA Setup portal can always be accessed by faculty and staff at www.lsue.edu/mfa. Please note that you will need access to at least one of your MFA verification methods to sign-in to the MFA setup portal, even if you are on campus.
What Methods Are Available for Faculty and Staff?
There are three different types of verification for faculty and staff:
- Phone Text - to a primary or an additional alternate phone number.
- Phone Call - to a primary or an additional alternate phone number. You must answer a phone call then press “#” on your phone at the automated prompt.
- Microsoft Authenticator app - notification which provides a quick Approve/Deny notification on your device.
You should configure one of the three methods as your primary method and preferably configure an extra alternate method to use as a backup (for example, you might lose your phone or not be able to receive a phone call—having access to a second method makes sure you always have the ability to access
your account). Ideally, you should have a backup method on a completely separate device
from your primary device. You can use an alternate authentication phone number that
is not tied to your primary phone as an example.
When configuring a phone number, we recommend using your personal cell phone number since this is the number that you will most likely have available to you when trying to log in from off-campus. It does not have to be a cell phone number (and it doesn’t have to be a smart phone, either), but please make sure that any number you use for MFA enrollment is one that you expect to have access to when trying to verify a sign in. The number you use for your authentication phone, or alternate authentication phone, will not be published or used for anything other than verifying your sign-in with Microsoft.
Please do not use your office phone as your primary verification method. MFA will be required when you are off-campus, so if you make your office phone the default verification method (or your only verification method), you will not be able to approve your valid logins and may not be able to access your account from off-campus.
I'm Already Enrolled. How Can Faculty/Staff Modify Enrollment?
You will need access to at least one of your previously enrolled factors. If you do not have access to any of your MFA factors, please try again later when you will have access or Contact OIT for an MFA reset if none of your factors are available to you anymore.
Access the MFA Setup portal by going to www.lsue.edu/mfa
You may be asked to sign in with your username and password. Then, you will have to verify your sign on with one of your enrolled factors.
The portal will show you all your currently configured or available MFA factors. For example, in the screenshot below, this user has the "phone text" method configured and set as default as well as a phone number to call along with the Microsoft Authenticator app enrolled.
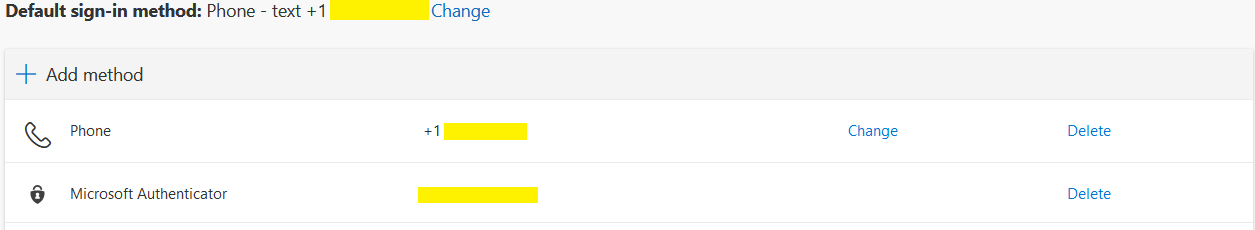
In this portal, you can delete, change, or add factors. Choose one of the highlighted links to make the appropriate change.
Click “add method” to add another factor, like an alternate phone or such. You will be required to verify any new method to confirm that it will work.
After making the required changes, don’t forget to check your default method before leaving the MFA portal.
Safe Links for Faculty/Staff Email
Microsoft Office 365 offers several services to protect users from malicious links and downloads. Office 365 Advanced Threat Protection Safe Links scans links for faculty and staff incoming email to protect employees from clicking on malicious, phishing, or spam links no matter where the user is connecting from and no matter what client is being used.
When Safe Links is enabled, employees may notice that the links in your email do not look as expected. This is because Outlook redirects the links through their Safe Links service to block access to a dangerous link. Because of this, you may need to change the way that you evaluate suspicious emails.
What Does Safe Links Look like?
If you are using Outlook Web Access (OWA) in your browser, Office 365 will show you the “Original URL” or “Protected by Outlook” link when you hover over it. You will still be able to evaluate the URL to determine if it looks suspicious or unexpected. When you click the link, you will still be sent through the Safe Links server and prevented from accessing sites that are determined to be malicious.

For other clients, the client will not present the "original" or "protected" links as seen in the previous example. If you hover over a Safe Links protected URL you will see safelinks.protection.outlook.com (or other similar iteration) followed by the original address within the email. This is normal and expected. In the example below, you will see the reference to Safe Links followed by the url=https://www.lsue.edu, which was the original address.
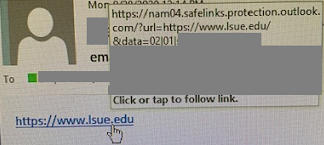
How Do I Know if a Link is Legitimate if I Can't Always See It?
- Use other indicators to determine the legitimacy of the email:
-
Do you know the sender?
-
Are you expecting a message from this user?
-
Does the context of this message make sense?
-
Has the email come from an email address you trust?
-
-
Is the message using pressure or threats to coerce you to click the link?
-
Is the sender threatening to “disable your email”?
-
Is the sender trying to coerce you to “validate your account” within a short period of time by threatening to disable your account or purge your information?
-
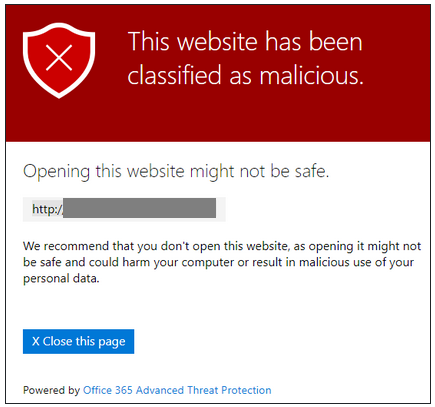
What Happens if I Click a Malicious Link?
Your browser will stop at the safelinks.protection.outlook.com domain and show you the following warning. No further action is necessary.
NOTE: If you feel a site has been blocked in error please forward the original email and link to it@lsue.edu.
Final Notes Regarding Safe Links
You can still send suspicious emails to it@lsue.edu.
If you think the email looks legitimate and click the link, Microsoft scans the contents of the site to determine if the link is legitimate. Microsoft uses intelligence gathered from emails and links across all Outlook users to help increase the likelihood malicious links will be stopped. In most cases, bad links will be caught automatically.
If you do not encounter the malicious link message, still evaluate the destination website for legitimacy.
- Are you being asked to sign in on a site with a strange or misleading domain?
- Does something about the site seem off (misspellings, broken links, outdated logos)?
If you think a destination site is malicious, you can report the message to it@lsue.edu for further evaluation. Additionally, you can wait and check the link again through the Safe URL redirect later. As Microsoft sees more instances of a link associated with a malicious domain, the Safe Links URL may block access to the destination URL after a few minutes pass.
Safe Attachments for Faculty/Staff Email
Microsoft Office 365 offers several services to protect users from malicious links and downloads. Office 365 Advanced Threat Protection Safe Attachments scans attachments in email messages you receive trying to find any malicious code or content. It even protects you when you access your email from a mobile device or from off the LSUE network.
How Does it Work?
For most all email messages, you won’t immediately notice any changes. You will see the entire message body and an icon for your attachments. However, if Microsoft is still in the process of scanning your attachment(s), you will see a placeholder that will let you know what is going on as shown in the image below. Safe Attachment scans typically complete within a couple of minutes so you likely will never notice this feature, but this could take a bit longer for large attachments.
![]()
While attachments are being scanned, Microsoft allows a preview of compatible attachment types, such as PDFs and Office documents, so you can begin viewing the content in safe mode without macros or other potentially harmful content. If the attachments are deemed safe, the placeholder is replaced with the original attachments.
Caution
Remember to only open attachments in messages sent by a reliable and verified source. If the sender’s email address looks suspicious or the message itself doesn't look right, do not open the attachment without checking with OIT. Safe Attachments provides an extra layer of protection, but it does not guarantee that all files are safe.
If you ever open an attachment and it looks suspicious or causes any concern, please take appropriate precautions and contact OIT.
Phishing is a top cybersecurity threat to LSUE. Phishing attacks are often launched by including malicious attachments or links within an email. Email being delivered from outside LSUE to faculty and staff should always be approached cautiously, especially messages that present urgency or fear, have poor grammar, and more.
To help combat phishing and assist faculty and staff with identify potentially fraudulent email, LSUE has activated external email tagging. Moving forward, messages sent from outside LSUE to any faculty and staff will now be marked with the following tagline at the beginning of the message:
“EXTERNAL EMAIL: Do not click links or attachments unless you recognize the sender and know the content is safe."
An example of how this tag will look within an external email as it is delivered to an employee is included here so you can see the formatting and such:
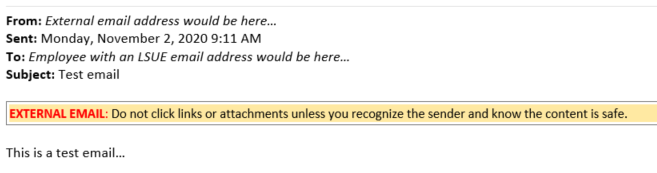
Many safe and legitimate email messages come from external email systems. The "External Email" tag does not mean the message is a scam, but it does provide additional information about the message source. The tag is simply there to assist employees by providing a reminder for you to stop and think about the email.
If you believe you have received a message that is malicious, is a phishing attempt, or you feel a message was improperly tagged, please Contact OIT.
Have you received a suspicious email in your faculty or staff Inbox? If you have, faculty and staff can easily report spam and phishing attempts through Microsoft Outlook's "Report Message" add-in feature.
Use of this feature notifies both Microsoft and LSUE OIT that a suspicious email been delivered to a member of our faculty or staff, which helps protect the University from cyberattacks. If the message is confirmed to be malicious, Microsoft will add this email to its filters to prevent it from reaching other people, and OIT can research and remediate any potential threats.
Additionally, this feature offers you another way to mark messages as junk or not junk.
To Utilize the Add-In
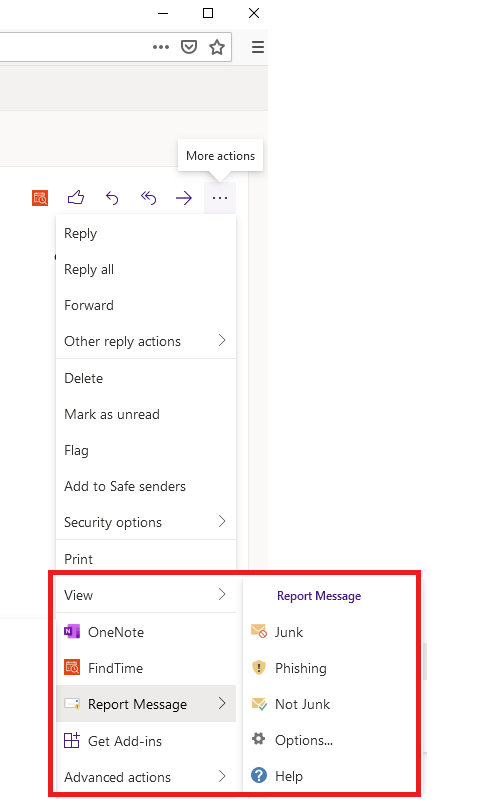
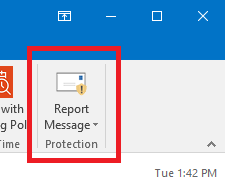
For those who read email via the Outlook desktop application
Once you open the email, locate the Report Message option in the upper right corner of your Outlook client. Select the option you are looking for (phishing, junk, etc) and then select "Report" to confirm your selection.
For those who read email via the Outlook web application
Once you open the email, click the ellipses in the upper right corner of your Outlook web client to expand the "More actions" area. From there, locate the Report Message feature from the list and then select the option you are looking for (phishing, junk, etc). Finally, select the "Report" option to confirm your selection.